Lorenz cipher
The Lorenz SZ40, SZ42A and SZ42B (SZ for Schlüsselzusatz, meaning "cipher attachment") were German rotor cipher machines used by the German Army during World War II. They were developed by C. Lorenz AG in Berlin. They implemented a Vernam stream cipher. British cryptographers, who referred to encrypted German teleprinter traffic as "Fish", dubbed the machine and its traffic "Tunny".[1]
The SZ machines were in-line attachments to standard Lorenz teleprinters. The SZ40 was introduced on an experimental basis in 1940. The enhanced SZ42 machines were brought into substantial use from mid-1942 onwards for high-level communications between the German High Command in Berlin, and Army Commands throughout occupied Europe.[2]
Wireless telegraphy (WT) rather than land-line circuits was used for this traffic.[3] These non-Morse (NoMo) messages were picked up by Britain's Y-stations at Knockholt and Denmark Hill and sent to Government Code and Cypher School at Bletchley Park (BP). Some were deciphered using hand methods before the process was partially automated, first with Robinson machines and then with the Colossus computers.[4] The deciphered messages made an important contribution to Ultra military intelligence.
Contents |
The Vernam cipher
Gilbert Vernam was an AT&T Bell Labs research engineer who, in 1917, invented a cipher system that used the Boolean "exclusive or" (XOR) function, symbolised by  .[5] This is represented by the following "truth table", where 1 represents "true" and 0 represents "false".
.[5] This is represented by the following "truth table", where 1 represents "true" and 0 represents "false".
| INPUT | OUTPUT | |
| A | B | A B B |
| 0 | 0 | 0 |
| 0 | 1 | 1 |
| 1 | 0 | 1 |
| 1 | 1 | 0 |
Other names for this function are: Not equal (NEQ), modulo 2 addition (without carry) and subtraction (without 'borrow').
In Vernam's cipher:
and:
which produces the essential reciprocity to allow the same machine with the same settings to be used for both enciphering and deciphering.
Vernam's idea was to use conventional telegraphy practice with a paper tape of the plaintext combined with a paper tape of the key. Each key tape would have been unique (a one-time tape), but generating and distributing such tapes presented considerable practical difficulties. In the 1920s four men in different countries invented rotor cipher machines to produce a key stream to act instead of a tape.[6] The 1940 Lorenz SZ40 was one of these, the revised 1942 versions were called the SZ42A and SZ42B.[7]
Structure
The logical functioning of the Tunny system was worked out well before the Bletchley Park cryptanalysts saw one of the machines—which only happened in 1945, shortly before the allied victory in Europe.[8]
The SZ machine served as an in-line attachment to a standard Lorenz teleprinter. It had a metal base 19 in (48 cm) × 15.5 in (39 cm) and was 17 in (43 cm) high.[7] The teleprinter characters consisted of five data bits, encoded in the International Telegraphy Alphabet No. 2 (ITA2). The enciphering machine generated a pseudorandom character-by-character key bit-stream that was XOR-ed with the input characters to form the output characters.[9]
Each of the five bits (or "impulses") of the key for each character was generated by the relevant wheels in two parts of the machine. The Bletchley Park analysts called these the 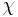 ("chi") wheels, and the
("chi") wheels, and the 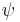 ("psi") wheels. Each wheel had a series of cams (or "pins") around them. These cams could be set in a raised (active) or lowered (inactive) position. In the raised position they generated a '1', in the lowered position they generated a '0'.
("psi") wheels. Each wheel had a series of cams (or "pins") around them. These cams could be set in a raised (active) or lowered (inactive) position. In the raised position they generated a '1', in the lowered position they generated a '0'.
The chi wheels all moved on one position for each character. The psi wheels also all moved together, but not after each character. Their movement was controlled by the two 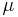 ("mu") or "motor" wheels.[10] The SZ40
("mu") or "motor" wheels.[10] The SZ40 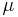 61 wheel moved one position with each character, but the
61 wheel moved one position with each character, but the 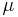 37 wheel moved on only when the cam on the
37 wheel moved on only when the cam on the 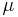 61 wheel was in the active position. If the cam on the
61 wheel was in the active position. If the cam on the 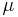 37 wheel was in the active position, all five psi wheels then moved.[10] The SZ42A and SZ42B models had additional complexity to this mechanism, known at Bletchley Park as Limitations.[11]
37 wheel was in the active position, all five psi wheels then moved.[10] The SZ42A and SZ42B models had additional complexity to this mechanism, known at Bletchley Park as Limitations.[11]
The key stream generated by the SZ machines thus had a chi component and a psi component that were combined together with the XOR function. Symbolically, the key that was combined with the plaintext for enciphering—or with the ciphertext for deciphering—can be represented as follows.[10]
 Psi-Key
Psi-KeyThe number of cams on each wheel equalled the number of impulses needed to cause them to complete a full rotation. It should be noted that these numbers are all co-prime with each other, giving the longest possible time before the pattern repeated. With a total of 501 cams this equals 2501 which is approximately 10151, an astronomically large number.[12] However, if the five impulses are considered independently, the numbers are much more manageable. The product of the rotation period of any pair of chi wheels gives numbers between 41×31=1271 and 26×23=598.
Operation
Each "Tunny" link had four SZ machines with a transmitting and a receiving teleprinter at each end. For enciphering and deciphering to work, the transmitting and receiving machines had to be set up identically. There were two components to this, setting the patterns of cams on the wheels and rotating the wheels for the start of enciphering a message. The cam settings were changed less frequently before the Summer of 1944. The psi wheel cams were initially only changed quarterly, but later monthly, the chi wheels were changed monthly but the motor wheel patterns were changed daily. From 1 August 1944, all wheel patterns were changed daily.[13]
Initially the wheel settings for a message were sent to the receiving end by means of a 12-letter indicator sent un-enciphered, the letters being associated with wheel positions in a book. In October 1942 this was changed to the use of a book of single-use settings in what was known as the QEP book. The last two digits of the QEP book entry were sent for the receiving operator to look up in his copy of the QEP book and set his machine's wheels. Each book contained one hundred or more combinations. Once all the combinations in a QEP book had been used it was replaced by a new one.[14] The message settings should never have been re-used, but on occasion they were, providing a "depth", which could be utilised by a cryptanalyst.[15]
As was normal telegraphy practice, messages of any length were keyed into a teleprinter with a paper tape perforator. The typical sequence of operations would be that the sending operator would punch up the message, make contact with the receiving operator, use the EIN / AUS switch on the SZ machine to connect it into the circuit, and then run the tape through the reader.[7] At the receiving end, the operator would similarly connect his SZ machine into the circuit and the output would be printed up on a continuous sticky tape. Because this was the practice, the plaintext did not contain the characters for "carriage return", "line feed" or the null (blank tape, 00000) character.[3]
Cryptanalysis
British cryptographers at Bletchley Park had deduced the operation of the machine by January 1942 without ever having seen a Lorenz machine, made possible because of a mistake made by a German operator.
Interception
Known by Y Station operators used to listening to Morse code transmission as "new music", originally Tunny traffic interception was concentrated at the Foreign Office Y Station operated by the Metropolitan Police at Denmark Hill in Camberwell, London. But due to lack of resource at this time (~1941) it was given a low priority. A new Y Station, Knockholt in Kent, was later constructed specifically to receive Tunny traffic so that the messages could be efficiently recorded and sent to Bletchley Park. The head of Y station, Harold Kenworthy, moved to head up Knockholt. He was later promoted to head the Foreign Office Research and Development Establishment (F.O.R.D.E).
Code breaking
On 30 August 1941, a 4,500 character message was transmitted from Athens to Vienna. However, the message was not received correctly at the other end, so (after the recipient sent an unencoded request for retransmission, which let the codebreakers know what was happening) the message was retransmitted with the same key settings (HQIBPEXEZMUG); a forbidden practice. Moreover, the second time the operator made a number of small alterations to the message, such as using abbreviations (The second message was only 4,000 characters long), allowing the code breakers to see the obscuring character sequence. From these two related ciphertexts, General John Tiltman and his Research team were able to recover both the plaintext and the keystream. Tiltman then handed the keystream to mathematician Bill Tutte, who after writing out by hand the original teleprinter 5 character Baudot code, made an initial breakthrough by recognising a 41 character repeat.[8] Over the following two months Tutte, and other members of the Research section worked out the complete logical structure of the cipher machine. This achievement was later described as "one of the greatest intellectual feats of World War II".[8]
Decryption machines: worlds first programmable computer
Several complex machines were built by the British to attack Tunny. The first was a family of machines known as "Heath Robinsons", which used two paper tapes, along with electro-mechanical logic circuitry, to find the pin wheel settings of the Lorenz machine. Because of the relatively slow speed at which the mechanical tape readers operated, Heath-Robinson could take up to eight weeks to break a single message. Heath Robinson also had major problems keeping the two paper tapes in synchronism.
The next was the Colossus, the world's first programmable electronic digital computer, operational from December 1943. This was developed by G.P.O. engineer Tommy Flowers at Dollis Hill in London (the Post Office research station). Like the later ENIAC of 1946, it did not have a stored program, and was programmed through plugboards and jumper cables. It was both faster and more reliable than the Heath Robinsons; using it, the British were able to speed up the process of finding the Lorenz pin wheel settings. Colossus used an optical tape reader which could be driven much faster than Heath-Robinson's. As a result, Colossus could break a message within a couple of hours. The limitation to the speed at which Colossus operated remained the speed at which the optical tape reader could be driven without the tape breaking. This was around 30 miles per hour (48 kph). Since Colossus generated the obscuring characters in its electronic circuitry, the synchronisation problem was completely eliminated. Colossus itself derived its clock signal optically from the sprocket holes down the middle of the paper tape, so it always remained in synchronism with the tape reader regardless of the speed at which it actually ran.
The third machine was the Tunny Emulator.[16] This machine was designed by Bletchley Park, based on the reverse engineering work done by Tiltman's team in the Testery, to emulate the Lorenz Cypher Machine. When the pin wheel settings were found by Colossus and manual cryptanalysis, the Tunny machine was set up and run so the messages could be read.
Testery executives and codebreakers
After the cracking of Tunny, a special team of Tunny message code breakers was set-up under Ralph Tester, most initially transferred from Alan Turing's Hut 8. The team became known as the Testery:
- Ralph Tester linguist and head of Testery
- Jerry Roberts shift-leader, linguist and senior codebreaker
- Peter Ericsson shift-leader, linguist and senior codebreaker
- Victor Masters shift-leader
- Denis Oswald linguist and senior codebreaker
- Peter Hilton codebreaker and mathematician
- Peter Benenson codebreaker
- Peter Edgerley codebreaker
- John Christie codebreaker
- John Thompson codebreaker
- Roy Jenkins codebreaker
- Tom Colvill general manager
By the end of the war, the Testery had grown to 9 cryptographers, 24 ATS girls with a total staff of 118, organised in 3 shifts working round the clock.
See also
Notes
- ^ Hinsley 1993, p. 141
- ^ Hinsley 1993, p. 142
- ^ a b Good, Michie & Timms 1945, p. 4 of German Tunny
- ^ Good 1993, pp. 160–165
- ^ Klein, p. 2
- ^ Klein, p. 3
- ^ a b c Good, Michie & Timms 1945, p. 10 of German Tunny
- ^ a b c Sale, Tony, The Lorenz Cipher and how Bletchley Park broke it, http://www.codesandciphers.org.uk/lorenz/fish.htm, retrieved 21 October 2010
- ^ a b Good, Michie & Timms 1945, p. 6 of German Tunny
- ^ a b c Good, Michie & Timms 1945, p. 7 of German Tunny
- ^ Good, Michie & Timms 1945, p. 8 of German Tunny
- ^ Churchhouse 2002, p. 158
- ^ Good, Michie & Timms 1945, p. 14 of German Tunny
- ^ Copeland 2006, p. 45
- ^ Churchhouse 2002, p. 34
- ^ Bletchley Park completes epic Tunny machine The Register, 26th May 2011, Accessed may 2011
References
- Churchhouse, Robert (2002), Codes and Ciphers: Julius Caesar, the Enigma and the Internet, Cambridge: Cambridge University Press, ISBN 978-0-521-00890-7
- Copeland, Jack (2006), "The German Tunny Machine", in Copeland, B Jack, Colossus: The Secrets of Bletchley Park's Codebreaking Computers, Oxford: Oxford University Press, ISBN 978-0-19-284055-4
- Davies, Donald W., The Lorenz Cipher Machine SZ42, (reprinted in Selections from Cryptologia: History, People, and Technology, Artech House, Norwood, 1998)
- Good, Jack (1993), "Enigma and Fish", in Hinsley, F.H.; Stripp, Alan, Codebreakers: The inside story of Bletchley Park, Oxford: Oxford University Press, ISBN 978-0-19-280132-6
- Good, Jack; Michie, Donald; Timms, Geoffrey (1945), General Report on Tunny: With Emphasis on Statistical Methods, UK Public Record Office HW 25/4 and HW 25/5, http://www.alanturing.net/turing_archive/archive/index/tunnyreportindex.html, retrieved 15 September 2010 That version is a facsimile copy, but there is a transcript of much of this document in '.pdf' format at: Sale, Tony (2001), Part of the "General Report on Tunny", the Newmanry History, formatted by Tony Sale, http://www.codesandciphers.org.uk/documents/newman/newman.pdf, retrieved 20 September 2010, and a web transcript of Part 1 at: Ellsbury, Graham, General Report on Tunny With Emphasis on Statistical Methods, http://www.ellsbury.com/tunny/tunny-001.htm, retrieved 3 November 2010
- Hinsley, F.H. (1993), "An introduction to Fish", in Hinsley, F.H.; Stripp, Alan, Codebreakers: The inside story of Bletchley Park, Oxford: Oxford University Press, ISBN 978-0-19-280132-6
- Klein, Melville, Securing Record Communication: The TSEC/KW-26, http://www.nsa.gov/about/_files/cryptologic_heritage/publications/misc/tsec_kw26.pdf, retrieved 17 September 2010
- Tutte, W. T., FISH and I Transcript of a lecture by Prof. Tutte explaining how he broke into Tunny.
- Entry for "Tunny" in the GC&CS Cryptographic Dictionary
- The Lorenz Cipher and how Bletchley Park broke it by Tony Sale
Further reading
- Stephen Budiansky, Battle of Wits (Free Press, New York, 2000). Contains a short but informative section (pages 312–315) describing the operation of Tunny, and how it was attacked.
- Paul Gannon, Colossus: Bletchley Park's Greatest Secret (Atlantic Books, 2006). Using recently declassified material and dealing exclusively with the efforts to break into Tunny. Clears up many previous misconceptions about Fish traffic, the Lorenz cipher machine and Colossus.
- F. H. Hinsley, Alan Stripp, Codebreakers: The Inside Story of Bletchley Park (Oxford University Press, 1993). Contains a lengthy section (pages 139–192) about Tunny, the British attack on it, and the British replicas of the Lorenz machine.
- Small, Albert W. (1944), The Special Fish Report, http://www.codesandciphers.org.uk/documents/small/smallix.HTM, retrieved 21 September 2010
- Michael Smith, Station X: Decoding Nazi Secrets (TV Books, New York, 2001). Contains a lengthy section (pages 183–202) about Tunny and the British attack on it.
External links
|
||||||||||||||||||||||||||||||||